Building Security Operation Centres
CND have been instrumental in building SOCs since before the turn of the century. We're completely flexible and available to support your own build team, deliver the entire build and hand it over, or anything in between.
Security Information Events Managers (SIEM) have enabled high level reporting of events from a single pane of glass and provide an invaluable contribution to effective analysis within a SOC.
The gathering of security events and the analysis of them is just a part of running a SOC, there are many other areas which must be considered, our consultants have been integral in the building of many SOCs from small businesses, through large enterprises with 100s of thousands of users, to Managed Security Service Providers who monitor numerous clients.
We do believe in practising what we preach and have our own SOCs which we run as an MSSP for small to medium size businesses. We also have our staff embedded into our clients SOCs to supplement their staff or as an on-premise managed service SOC Staffing. Finally, we also conduct Maturity Assessments and offer a number of associated services for existing SOCs.
SOC Build as a Service
Whilst we will continue to build SOCs for our clients with agility in whatever way they want, for ultimate flexibility in delivery, you can engage us to build your SOC (or part therein) as a service, where we manage the process from start to finish, you decide on your level of involvement and we agree on the project milestones.
We then supply the necessary consultants and as the build develops consider rotating them out for more appropriate consultants, for example as the build moves from governance, to implementation and to operation. All the while parachuting in subject matter experts to efficiently handle those very specialised tasks and dare we say, inevitable problems.
Over the years, this approach has proved to be increasingly popular with both our clients and partners. The traditional approach of having specific consultants to deliver the entire project proved to be too rigid and inefficient. Moreover, it all too often fell foul of UK tax regulations.

SOC Build Modules
We are extremely flexible in how we deliver SOCs, as there is no one-size-fits-all. At CND we offer an extremely flexible "pick 'n' mix" approach, where clients can choose what they would like from a range of dozens of SOC modules. Below is a very high level overview where we break down some of the modules from conception through to delivery:
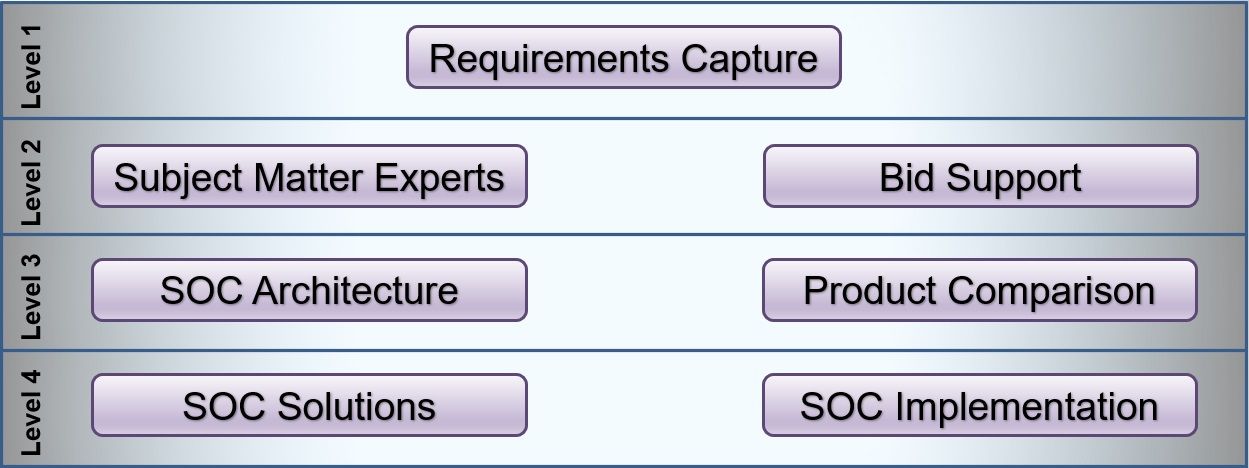
Requirements Capture
Understanding what the mandatory and desirable SOC requirements are. There are 100's of potential requirements which might include:
- Hours of Operation
- Event Coverage
- Speed of Response
- Event Retention
- On-Premise, Cloud, or Hybrid
- Much More
Experts
Whether you want a single subject matter expert to provide some guidance, or an entire SOC build team full time, we have consultants on hand to assist.
Bid Support
We are often called upon by contract primes to support them in a SOC Build bid submission. We have the experience and evidence of delivery for the bid submission, as well as the capability to surge manpower for the delivery when you win.
Architecture
Our security architects will work to your requirements and produce world class designs from solution overviews through to high and low level designs and down to step by step installation instructions. If required, we can be on hand for the full lifecycle of the SOC and it's products within, including tech refreshes.
Product Analysis
Not all SOC solutions are the same and finding the right product which "actually" meets your requirements can prove difficult. Our subject matter experts will work with you to narrow the field and if required run a proof of concept to verify suitability.
Reselling
We offer a number of security solutions for resale and because it isn't core to what we do, we can offer extremely competitive pricing. It should be noted that we remain fiercely vendor neutral and whilst we believe that the products we resell are best of breed, they aren't always best suited for a clients requirements and as a result we cannot always resell the products we feel are best for your SOC.
Implementation
Regardless of whether it is our design or not, our subject matter experts are on hand to install, configure and tune the deployment.
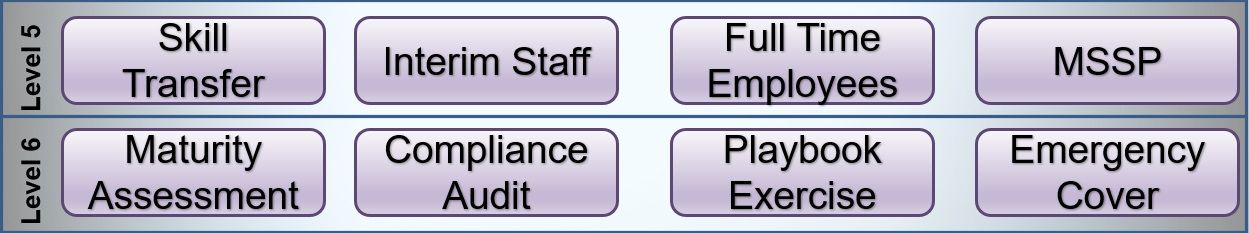
Skill Transfer
Part of our SOC Maturity Service, our subject matter experts will sit alongside your security engineers and/or analysts and train them.
Interim Staff
Part of our SOC Manning service. We can supply interim staff (contractors) to support you in your SOC.
Permanent Staff
It isn't always easy to find quality SOC staff, we have found individuals and even entire teams, using our specialist cyber security recruitment team.
MSSP
Part of our Managed Detection & Response Service, we provide a number of managed SOC services where a client can outsource all or part of their management and monitoring to us.
Maturity Assessment
Part of our SOC Maturity Service. Where you already have a SOC, our subject matter experts will evaluate it and advise on any gaps in capability.
Compliance
Part of our SOC Maturity Service. Our consultants will audit your SOC against a number of security frameworks, such as PCI DSS, NIST etc and/or Industry Best Practice and report on any capability gaps.
Exercise
Part of our SOC Maturity Service. Are you prepared for an incident? Our consultants will run your SOC through various scenarios and evaluate their response. These can be table top exercises or actual (but benign) events which appear on the consoles.
Cover
Part of our SOC Staffing Service. If you require staff at very short notice we are on hand to help. We also offer an Incident Response Service should it be for a breach. Service: Incident Response
Previous Client Engagement Examples
As SOC build veterans with decades of experience in building numerous SOCs, there is nothing that fazes us. We are vendor neutral and have worked with almost every security technology out there, we also have an extended global pool of Associate Partners who have some extremely specialist skills who we can call upon if required.
Below are a handful of SOC build projects we have worked on for our clients over the years:
Breach
Our client was breached and had no monitoring capability. Our Incident Response Team, triaged the incident within the hour and we had sensors in place shortly after, monitoring internal activity as well as IDS monitoring the boundaries, this all reported into our SOC under the MSSP service, whilst our Incident Response Team got to the root cause. After the 2 week "trial" the client signed up for the MSSP whilst we helped them develop their own monitoring capability.
Urgent SOC
Our client had an urgent need for a fully functioning SOC from a few sensors and their preferred SIEM. We sent in a SOC build veteran to gather the requirements and a project manager to form a plan which met the 3 week deadline. A security engineer got it all working and once it was reporting, an analyst started to work with the engineer to tune it. By the 3 week go live date, we had a shift system of our analysts and our recruitment team was finding permanent staff to replace them.
Cloud SOC
Our client already had an established on-premise SOC, but had a requirement for it to migrate to the Cloud. Our SOC architectural team designed and implemented a solution which is nearing operation.
MSSP
Our client is now an MSSP household name and whilst they had a SOC it was not suited to an MSSP. We were engaged to build them a capability around a SIEM for which they had an enterprise license.
Fresh Start
Our client had been offered a proof of concept SOC of a complete solution which they were unhappy with. We were given a meagre budget, within which we need to build a Detection and Response capability. After capturing the requirements, we set about designing a solution, which was accepted by the client. We then implemented the design which proved so popular with the client that we were referred to another client to repeat the design.
Helping Out
Our Defence client needed some expertise to assist them in the design and build of a global SOC. We supplied them with a subject matter expert who was embedded within the organisation for an extended period. As the SOC reached Interim Operational Capability, we were approached for more Senior SOC analysts, threat hunters and security engineers to be embedded within the organisation to work alongside military staff and provide skill transfer.