CND News and Blog
Top Tip - Start Looking Early in Your Second Year So, you're a university student dreaming of a third-year cybersecurity placement. You've survived fresher's week, learned that "phishing" isn't about trout, and mastered the art of submitting assignments 3 minutes before the deadline. Progress! But now comes the real boss level: finding a cyber...
Boston here we come! For those who've not yet had the opportunity to travel to a Splunk .conf event, it really is an event to behold. Big corporations with stock market listings are often necessarily conservative and perhaps, a bit dull. Splunk has none of that going on, if you're a cyber security professional this is a great annual occasion to rea...
Splunk reaches double digit maturity! I was very surprised on Tuesday to receive a nudge from a fellow Splunk Professional Services (PS) consultant, saying that Splunk 10.0 had been released overnight with almost no fanfare or mention. Splunk first released their Data-to-Everything platform in 2004 and has been ingesting data logs as the leadi...
Celebrating Neurodiversity As our company name, Computer Network Defence Ltd, suggests, we monitor business networks and catch computer hackers. When an incident is detected, we need our highly trained analysts to investigate the activity and triage the threat as quickly as possible. We feel this is best achieved by embracing diversity in all its f...
Introduction Microsoft 365 offers powerful collaboration and productivity tools, but default settings often leave numerous security gaps. This post aims to highlight five common misconfigurations we frequently encounter in our audits, along with practical steps to address them. During this post, we'll look at the following five areas: Security Defa...
Lets start with what is CAPTCHA? CAPTCHA is an acronym that stands for "Completely Automated Public Turing Test to tell Computers and Humans Apart" and is a type of challenge-response test used in computing to determine whether the user is human, and in doing so deter bot attacks and spam. Everybody that uses the internet regularly would have ...
Introduction In a significant development for social media users in the EU, the Appeals Centre Europe (ACE) has been launched to handle complaints against major platforms like Facebook, TikTok, and YouTube. This new independent body aims to streamline dispute resolutions under the EU Digital Services Act (DSA), providing users with a centralised me...
Overview This blog post introduces the concept of emergency access accounts—what they are, why they're essential, and how to manage them securely, including recent recommendations for authentication. The post will focus on M365 controls but the general concepts can be taken away. What are Emergency Access Accounts? An emergency account, sometimes c...
Introduction In a landmark decision, the European Union's top court, the Court of Justice of the European Union (CJEU), has ruled against Meta's data retention practices. This ruling has significant implications for how Meta, and other Ad-funded social networks, operate within the EU. The decision enforces the data minimisation principles of the Ge...
New Alerts for IBM, Dell, Xerox, Mozilla, and Linux. IBM IBM has published Critical bulletins for QRadar SIEM and Engineering Lifecycle Management.More info. Dell Dell has published a Critical bulletin for Networking SmartFabric Storage Software.More info. Xerox Xerox has published patches for third-party software included in Free...
Scams have been around for as long as people have been trading, but the rise of the internet has opened the floodgates for increasingly sophisticated cons. One of the latest and most devastating types is known as the "pig butchering" scam. Despite its unusual name, it doesn't have anything to do with farm animals. It's a financial fraud that preys ...
Computer Network Defence proudly celebrated its 20th anniversary with a Garden Party. The celebration, held at the Digital Mansion, Corsham, brought together employees, their families some travelling in from America, Isle of Man and various areas of the UK to commemorate two decades of dedication, innovation, and success. Founded in 2004, CND has g...
A couple of weeks ago a new version of Splunk was released: 9.2.2, this included various CVE resolutions (URL) and many of our clients have already rapidly responded and upgraded their version of Splunk. Upgrading is a quick and fairly low effort, low risk exercise so long as you haven't allowed tech-debt to creep into your infra. However once your...
CND sent two senior members of the team to Splunk Conf.24 in Las Vegas. The following is their account. 'We started the conference by attending talks by Splunk CEO Gary Steele who delivered the opening keynotes along side Cisco Present Chuck Robbins. With Splunk's recent merging with Cisco everyone was intrigued to see whether there would be ...
Ethical hacking, penetration testing, red teaming, offensive security. Those words evoke an image of someone with a black hoodie up, coding whilst a wall of binary scrolls slowly behind. The binary is usually green for good measure. So, over the last few years this has become to de facto 'cool' job. The idea of using malicious techniques, developin...
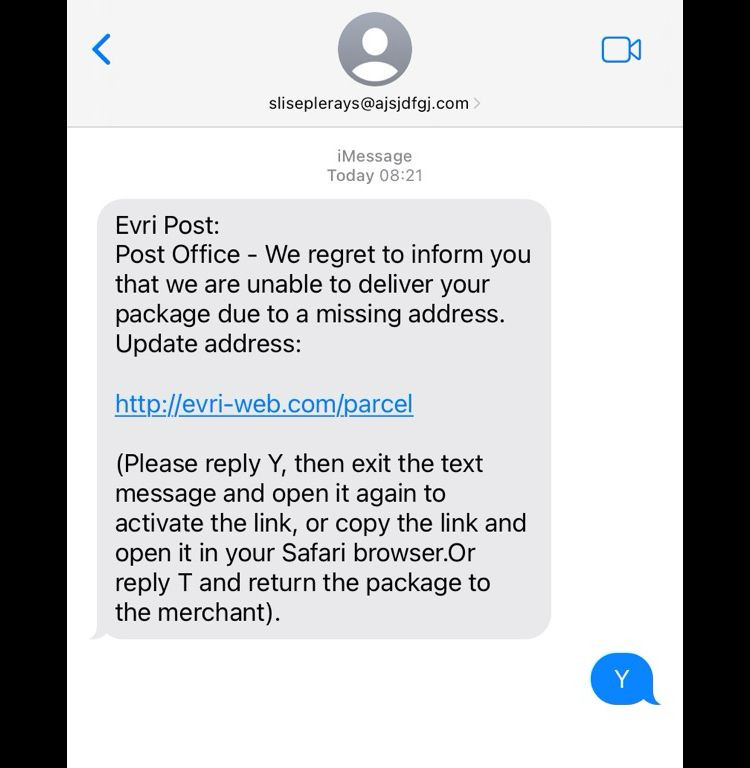
Scamming is sadly a daily risk whilst navigating cyberspace. I wrote almost exactly 3 years ago in different post about a similar postal scam, masquerading as the Post Office asking for a small missed delivery fee (URL). Well this week it happened again to a family member who started to fall for it, fortunately they stopped but ...
In today's modern world, the risk of cyber threats have increased significantly. With 5.16 billion people globally using the internet, you can understand how the use of hacktivism has increased The question we are asking today, is hacktivism a threat and what is it's impact on everyday society? In today's blog, we will explore this question further...
There is no doubt you have heard the word 'hacker' in recent years, but are you familiar with the word hacktivist and what this means? Today we are going to explore what is a hacktivist, what is their purpose, why they perform some of their acts and what the difference is between hackers and hacktivists. What is a simple definition of hacktiv...
As Gold ERS holders, we are lucky to have access to unique opportunities. In Summer 2023 CND were invited to attend the RAF Halton 'Employer Engagement Management and Leadership Experience'. This was a national event with over 50 participants from a variety of industries, taking part. Upon arrival, on a rather drizzly day the attendees were s...
During Summer 2023, members of the CND team had the privilege of attending the Defence Academy in Shrivenham. The aim of the visit was for members from private sector organisations and businesses who employ or sponsor RFCA personnel to view the facilities and receive an introduction to the purpose and function of the Defence Academy, arranged by We...
By accepting you will be accessing a service provided by a third-party external to https://www.cndltd.com/