CND News and Blog
Boston here we come! For those who've not yet had the opportunity to travel to a Splunk .conf event, it really is an event to behold. Big corporations with stock market listings are often necessarily conservative and perhaps, a bit dull. Splunk has none of that going on, if you're a cyber security professional this is a great annual occasion to rea...
The Cyber Threat Intelligence page, affectionately known as the Radar Page by some (or maybe just me), has been around for over 13 years. See the Daily Mail article below for the sensational history. :) It has been through several redesigns, but retains a similar look and feel across the versions. Where to find the Radar Page: The...
Splunk reaches double digit maturity! I was very surprised on Tuesday to receive a nudge from a fellow Splunk Professional Services (PS) consultant, saying that Splunk 10.0 had been released overnight with almost no fanfare or mention. Splunk first released their Data-to-Everything platform in 2004 and has been ingesting data logs as the leadi...
Introduction Microsoft 365 offers powerful collaboration and productivity tools, but default settings often leave numerous security gaps. This post aims to highlight five common misconfigurations we frequently encounter in our audits, along with practical steps to address them. During this post, we'll look at the following five areas: Security Defa...
Lets start with what is CAPTCHA? CAPTCHA is an acronym that stands for "Completely Automated Public Turing Test to tell Computers and Humans Apart" and is a type of challenge-response test used in computing to determine whether the user is human, and in doing so deter bot attacks and spam. Everybody that uses the internet regularly would have ...
Introduction In a significant development for social media users in the EU, the Appeals Centre Europe (ACE) has been launched to handle complaints against major platforms like Facebook, TikTok, and YouTube. This new independent body aims to streamline dispute resolutions under the EU Digital Services Act (DSA), providing users with a centralised me...
Overview This blog post introduces the concept of emergency access accounts—what they are, why they're essential, and how to manage them securely, including recent recommendations for authentication. The post will focus on M365 controls but the general concepts can be taken away. What are Emergency Access Accounts? An emergency account, sometimes c...
Introduction In a landmark decision, the European Union's top court, the Court of Justice of the European Union (CJEU), has ruled against Meta's data retention practices. This ruling has significant implications for how Meta, and other Ad-funded social networks, operate within the EU. The decision enforces the data minimisation principles of the Ge...
Scams have been around for as long as people have been trading, but the rise of the internet has opened the floodgates for increasingly sophisticated cons. One of the latest and most devastating types is known as the "pig butchering" scam. Despite its unusual name, it doesn't have anything to do with farm animals. It's a financial fraud that preys ...
A couple of weeks ago a new version of Splunk was released: 9.2.2, this included various CVE resolutions (URL) and many of our clients have already rapidly responded and upgraded their version of Splunk. Upgrading is a quick and fairly low effort, low risk exercise so long as you haven't allowed tech-debt to creep into your infra. However once your...
CND sent two senior members of the team to Splunk Conf.24 in Las Vegas. The following is their account. 'We started the conference by attending talks by Splunk CEO Gary Steele who delivered the opening keynotes along side Cisco Present Chuck Robbins. With Splunk's recent merging with Cisco everyone was intrigued to see whether there would be ...
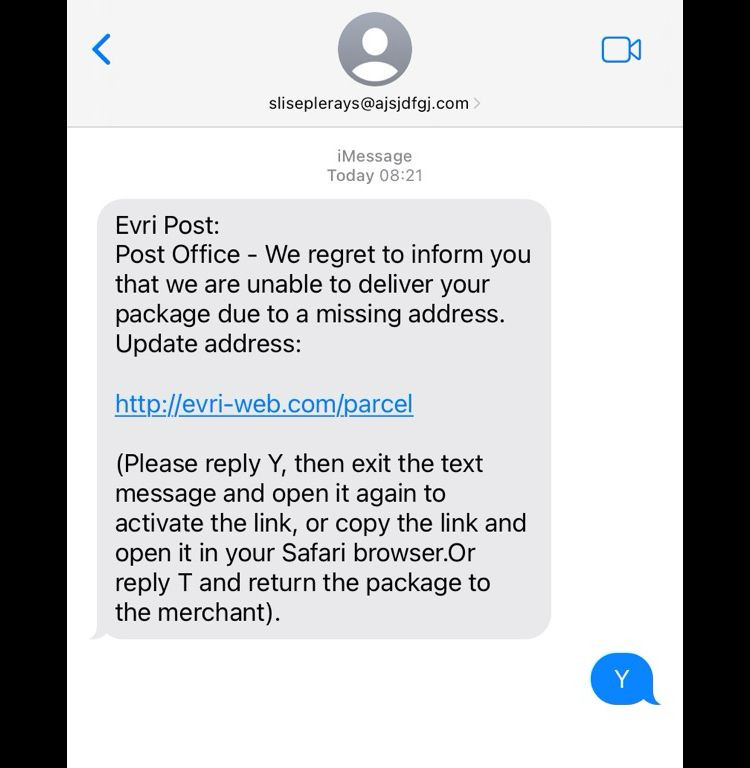
Scamming is sadly a daily risk whilst navigating cyberspace. I wrote almost exactly 3 years ago in different post about a similar postal scam, masquerading as the Post Office asking for a small missed delivery fee (URL). Well this week it happened again to a family member who started to fall for it, fortunately they stopped but ...
In today's modern world, the risk of cyber threats have increased significantly. With 5.16 billion people globally using the internet, you can understand how the use of hacktivism has increased The question we are asking today, is hacktivism a threat and what is it's impact on everyday society? In today's blog, we will explore this question further...
There is no doubt you have heard the word 'hacker' in recent years, but are you familiar with the word hacktivist and what this means? Today we are going to explore what is a hacktivist, what is their purpose, why they perform some of their acts and what the difference is between hackers and hacktivists. What is a simple definition of hacktiv...
A collection of 21 security flaws have been discovered in Sierra Wireless AirLink cellular routers and open-source software components like TinyXML and OpenNDS. Collectively tracked as Sierra:21, the issues expose over 86,000 devices across critical sectors like energy, healthcare, waste management, retail, emergency services, and vehicle tracking to cyber threats, according
In an increasingly complex and fast-paced digital landscape, organizations strive to protect themselves from various security threats. However, limited resources often hinder security teams when combatting these threats, making it difficult to keep up with the growing number of security incidents and alerts. Implementing automation throughout security operations helps security teams alleviate these challenges by streamlining repetitive tasks, reducing the risk of human error, and allowing them to focus on higher-value initiatives.
While automation offers significant benefits, there is no foolproof method or process to guarantee success. Clear definitions, consistent implementation, and standardized processes are crucial for optimal results. Without guidelines, manual and time-consuming methods can undermine the effectiveness of automation.
This blog explores the challenges faced by security operations teams when implementing automation and the practical steps needed to build a strong foundation for successful implementation.
The Automation Challenge
Organizations often struggle with automation due to a lack of well-documented processes and limited resources. With constant alerts and fires to put out, security teams are often spread thin, and only have time to focus on the task in front of them. This leaves them little to no time for proper documentation of processes and procedures. This, along with other factors such as maturity and process monitorability, contributes to the challenges security teams face when implementing automation. Successful automation requires a pragmatic approach, where teams identify and prioritize processes that are feasible and provide the greatest impact on efficiency and risk reduction.
Last week I was able to attend the CyberThreat 23 (CT23) conference in London, held by SANs and the National Cyber Security Centre (NCSC) The conference has been running for a few years now and from SANs marketing material the event is: Designed for security practitioners and spanning the full spectrum of offensive and defensive discipline, t...
TLDR: Building a Splunk Test instance is really useful, helps protect against prod outages and very performant hardware is now available for a fraction of the price it used to be; if you're willing to deal with some tech challenges! Splunk Test instance Many of our clients rely on Splunk as their production SIEM tool to monitor, detect and respond ...
As my PA-220 firewall heads towards EoL I swapped it out for a PA-410 and OS 11.x I've worked professionally with firewall platforms for nearly 20 years, during that time I've configured Netscreen, Juniper, Palo Alto and Cisco to name a few of the dominant vendors. The most admin friendly and enjoyable platform to work with in m...
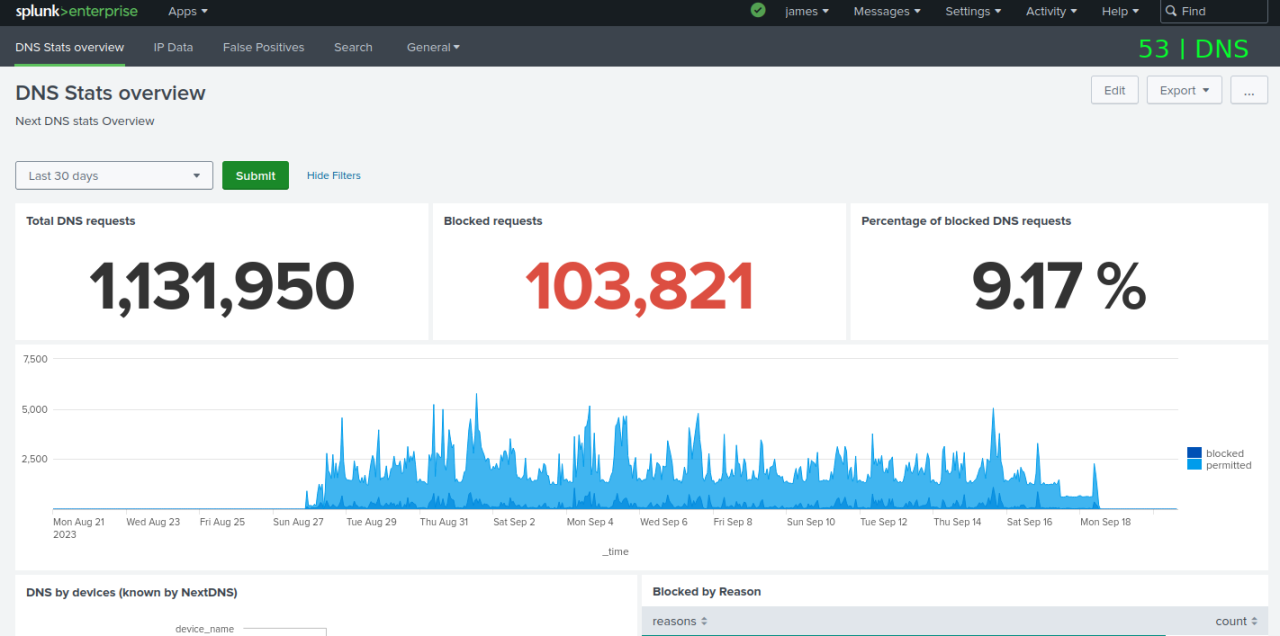
I was listening to an InfoSec podcast on the drive back from a client recently (Privacy, Security & OSINT Show) it's a really good listen and I really appreciate Michael Bazzells work. One of the items in the podcast was NextDNS, a product which I've not come across before. NextDNS operates by you registering an account for a very mod...
By accepting you will be accessing a service provided by a third-party external to https://www.cndltd.com/