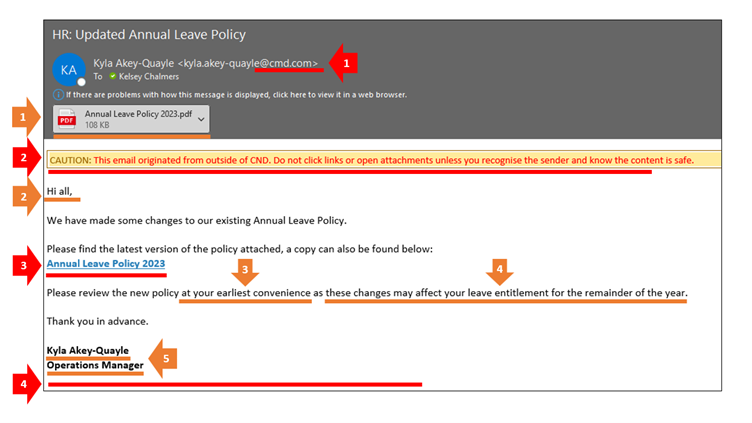
This simulated phishing email had two possible failure actions – clicking on the link or opening the PDF attachment. It was a particularly difficult scenario as it appeared to come from a real member of the CND team, however, there were a few indicators (red and amber flags) which could have been spotted.
The reason we have labelled some of these as amber flags, rather than red, is because while they could be an indication of a phishing email, it is plausible that these would be used in real internal emails. If these amber flags are spotted within an email, while they may not mean that the email is a phishing attempt, spotting them should prompt you to carry out a thorough check of the entire email to look for any other possible flags.
Below we have provided the reasons for each of these flag
Red Flags
1. The domain name appears to be coming from within the organisation, however, it is misspelt (there is an 'M' in place of the usual 'N' within CND).
2. The purpose of this external tag is to let us know that the email is coming from outside of our organisation, as this email is claiming to be coming from a member of the CND team, we should not be seeing this external tag.
3. If you had hovered over the link, you would have seen that the link was taking you to a different site than the email content said it would.
4. There is no CND email signature.
Amber Flags
1. Not all attachments are bad, however, they should be treated as equally suspicious as links. Any time you receive an email with an attachment, you should be carefully checking the entire email for any possible flags.
2. Generic greetings such as 'Hi all' can be a red flag, however, as this email was sent to the whole company, this is something we might expect to see when an updated policy has been sent out to everyone.
3 .Phishing emails will often use wording such as 'at your earliest convenience' to create a sense of urgency to encourage you to click the link or open the attachment without first taking the time to consider the authenticity of the email. However, if an internal policy was updated, we would expect to see this wording used, therefore, in this instance, this is an amber flag rather than red.
4. The email also suggests that there may be a negative impact if the email is ignored. Again, this wording is often used in phishing emails to alarm the reader and encourage them to click the link/open the attachment. Once again, as we would expect to see this wording in an internal email is a policy was being updated with changes which might affect the reader, this has been flagged as amber in this instance.
5. Just because the email uses the name and position of a real person within the organisation, do not assume that this means the email is genuine, as this information is easily accessible on both the company website and LinkedIn.
If your team received an email like this, are you confident that they would recognise it as a phishing attempt?
Our Managed Cyber Education Service allows you to not only test your users' ability to recognise phishing emails, but also provide them with instant training to reinforce their learning.
If one of your users carries out a failure action upon receiving a simulated phishing test (e.g., clicking on a link, opening an attachment, scanning a QR code, or inputting data into a credential harvesting page), they will immediately be re-directed to a landing page which will highlight each of the red flags they could have spotted within the email to provide them with instant training.
The platform we utilise also has a built-in learning management system which offers over 1,400 training modules in a number of formats including interactive modules, videos, games and posters. These modules cover a range of different security awareness topics, including, but not limited to:
- Phishing
- Data Protection
- Passwords & Authentication
- Incident Reporting
- Physical Security
- Email, Internet and Social Media
- Mobile Devices
Not only can we manage this service for you, we are also a trusted partner of the platform provider and can provide you with the licensing to manage the service internally, if preferred.
Should you choose to have us manage the service for you, our team of security awareness consultants will assist you with any necessary onboarding steps such as allow listing, user provisioning and installing the reporting function (if required).
Once your account is setup, our consultants will use their security background and knowledge of the platform to create you a customised plan with tailored phishing scenarios and a suggested training programme, along with proposed dates and any other associated information, for you to review and approve.
If you would like to learn more about our Managed Cyber Education Service, or the platform itself, please contact