As my PA-220 firewall heads towards EoL I swapped it out for a PA-410 and OS 11.x
I've worked professionally with firewall platforms for nearly 20 years, during that time I've configured Netscreen, Juniper, Palo Alto and Cisco to name a few of the dominant vendors. The most admin friendly and enjoyable platform to work with in my opinion is Palo Alto. I first encountered them in 2013 with the 5000 series and OS4.x which was being used at a top tier financial institution for low latency trading.
Whilst there are some nuances to setting up your terminal and outputting the config in 'set' based format rather than XML it quickly shows its strength as an engineer friendly platform. Unusually it has an excellent GUI, why would I use the GUI as a professional I hear you say? Good question, they've done a really good job of making it intuitive and the live monitoring 'Session Browser' is a quick and easy means to see sessions passing through the firewall. There are also software and dynamic updates pages which can make small scale upgrades quicker through the UI.
In January 2023 the EoL bulletin was updated with the PA-220 end of sale date and the last supported OS as 10.2.x (URL). OS 11 was released in May this year and it's clear that the writing is on the wall for my trusted platform. I wasn't entirely sad about this as the commit speed felt quite slow with perhaps an underpowered CPU.
My use case in this instance is as a SoHo deployment, used to protect my work assets, home LAN and guest networks whilst providing logical isolation. With individuals more frequently working from home since 2020 there are more risks with domestic networks particularly for those who have flat networks with all nodes sharing the same segment. Using the Palo Alto firewall I'm able to simply isolate Home, Work, Smart TV's and multiple Wi-Fi networks and ensure never the twain shall meet.
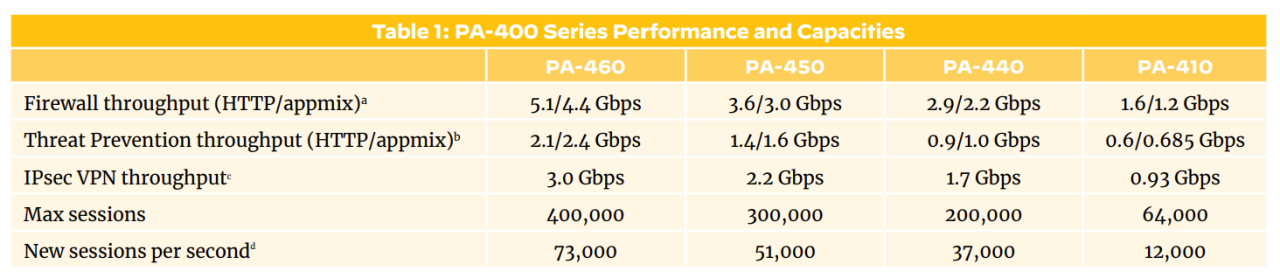
One item that has changed in the past few years is ISP bandwidth and fibre to the premises (FTTP) becoming increasingly available. The 220 had a maximum backplane throughput of approx. 500Mbp/s depending on the exact type of traffic passing through the data-plane. I hope soon to have 1Gbp/s and it would be a shame to halve the potential ISP bandwidth with my firewall platform. The PA-400 series benefits from a significant uplift:
So my new platform arrived and I was excited to get started on the preparation to swap it out, I have a USB A to console cable and connected it to my Linux laptop, it is fairly similar on a mac. Having powered up the platform I needed to connect via terminal to get the basics set.
# About:
This config config guide will guide through the initial steps of connecting to the Palo Alto Firewall on a linux platform.
## Install screen app
<pre>
sudo apt-get install screen
</pre>
## Determine Port
<pre>
sudo dmesg | grep -i tty
</pre>
- Example:
- notice final line 'ttyUSB0
<pre>
[ 0.016142] ACPI: SSDT 0x0000000063FAD000 000FBB (v02 DELL TbtTypeC 00000000 INTL 20180927)
[ 0.086350] printk: console [tty0] enabled
[ 4.347237] dw-apb-uart.2: ttyS4 at MMIO 0x4010002000 (irq = 20, base_baud = 7500000) is a 16550A
[ 17.544318] Bluetooth: RFCOMM TTY layer initialized
[545508.206747] usb 3-4: FTDI USB Serial Device converter now attached to ttyUSB0
</pre>
## Establish connection:
- Note the stty parameter sets the baud rate etc, without this the output will be difficult to work with or nonsense chars.
<pre>
stty -F /dev/ttyUSB0 9600 cs8 -cstopb -parenb
sudo screen /dev/ttyUSB0
# press enter
# You should now have access
username: admin
password: admin
With that set and basic access established there are a few more basics to sort out before ethernet based MGT access is available. If you have Panorama and a larger enterprise deployment then there is the option of ZTP, otherwise:
## Remove ZTP mode: - Zero Touch Provisioning, remove if you don't have Panorama - [Palo Alto, ZTP](https://www.paloaltonetworks.com/cyberpedia/what-is-zero-touch-provisioning-ZTP) <pre> set system ztp disable # This will reset the firewall and reboot it # After reboot you may see PA-HDF login. # Ignore this and press return several times username: admin password: password </pre> ## Password: - <strong> Whoa there Cowboy! get your password manager out and generate a robust password </strong> - The world is a dangerous place, make sure it is strong and complex, do not help your adversary. <pre> # Set the new password per the prompt PA-410 login: admin Password: Last login: Fri Sep 15 08:51:05 on ttyS0 Enter old password : Enter new password : Confirm password : Password changed # Exit, logout of the terminal, check the new admin password works </pre> ## Process: - Set the CLI to 'set' based output, other options are JSON and XML. - Humans tend to prefer 'set' based format <pre> set cli config-output-format set configure show </pre>
With a strong and unique password set it's time to set the management IP and upgrade the factory installed software and dynamic updates:
## Set Management Interface
- You may wish to download the CLI guide:
- [Palo Alto CLI guide](https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-cli-quick-start/cli-cheat-sheets)
<pre>
show deviceconfig system
# default is:
set deviceconfig system ip-address 192.168.1.1
set deviceconfig system netmask 255.255.255.0
</pre>
- Change the IP and Mask as appropriate
- Example below is a simple example
<pre>
admin@PA-410# set deviceconfig system ip-address 10.x.x.x
[edit]
admin@PA-410# commit
<Enter> Finish input
admin@PA-410# commit
Commit job 3 is in progress. Use Ctrl+C to return to command prompt
....................55%.....70%.98%...................100%
Configuration committed successfully
Warning: zone "trust": log-setting is not configured, logs will not be forwarded.
Warning: zone "untrust": log-setting is not configured, logs will not be forwarded.
Warning: security rulebase "rule1": log-setting is not configured, logs will not be forwarded.
</pre>
## SSH check
* Now that you have set the basics, you may want to switch to SSH to take advantage of a faster baud rate, remote access.
<pre>
ssh -o HostKeyAlgorithms=+ssh-rsa admin@10.x.x.x
</pre>
## Operational commands
- [Palo Alto, CLI cheat sheet](https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-cli-quick-start/cli-cheat-sheets/cli-cheat-sheet-device-management)
## Check the current state:
<pre>
show system info
# OR
show system info | match sw-version
</pre>
### Content updates:
* Upgrading the content may be a pre-requisite before upgrading.
<pre>
request content upgrade check
request content upgrade download latest
# This will initiate a job, you can check jobs:
show jobs all
# re-check the status and upgrade it
request content upgrade info
request content upgrade install version latest
</pre>
Note: without a custom SSH profile setup to comply with modern standards you're likely to have to issue the SSH with an option command to allow ssh-rsa (you can fix this later). Having committed the changes time to upgrade.
Bleeding edge (11.0.2-h2)
Software strategy is an important consideration for any enterprise, it may be that you require new features or simply wish to negate any CVE's with the latest patches. I decided to go straight to the latest release which is 11.0.2-h2. This ended up being a mistake and cost me around 2hrs to figure out the problem and solution.
The issue was that as I built up the platform using my existing config the 'auto-commit' job kept running and getting stuck. I killed the job using the cli and reset the process but it kept being an issue. Eventually I managed to kill it and downgrade the platform to 11.0.2 but it was a good reminder that the appetite for bleeding edge releases may not be appropriate for all organisations.
## Upgrade the software * See the CLI reference guide also: * [Palo Alto, use CLI for upgrade tasks](https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-upgrade/cli-commands-for-upgrade/use-cli-commands-for-upgrade-tasks) <pre> show system info request system software check admin@PA-410> request system software check Version Size Released on Downloaded ------------------------------------------------------------------------- 11.0.2 595MB 2023/06/28 12:13:00 no 11.0.2-h1 596MB 2023/08/16 14:25:46 no 11.0.1-h2 510MB 2023/05/30 13:11:19 no 11.0.1 510MB 2023/03/29 15:05:41 no 11.0.0 898MB 2022/11/17 08:45:06 yes 10.2.5 656MB 2023/08/17 12:40:56 no 10.2.4-h4 644MB 2023/07/27 11:02:36 no #Excerpt... admin@PA-410> request system software download version 11.0.2 </pre>
Having downloaded the updates, setup NTP, Syslog and ensured that my logs were arriving in Splunk I set about porting over the interfaces config, zones and security policies section by section using ssh with regular commits. I note that there were approximately 8000 lines of 'content-preview' configuration in the PA-220 running-config. I simply used 'sed' to delete this cruft:
sed 'set shared content-preview/d' PA-220-cleaned.conf
Again I performed all of this using the CLI via a Bash shell. If your organisation only allows you to have Windows consider requesting WSL (Windows Sub-system Linux) to make your life much easier and take advantage of a *nix like shell.
With my config committed and service routes set, I placed it in the cabinet and crossed fingers that I'd completed the conversion successfully. The boot time appears much quicker on the 410 than the 220 and I think within approx. 3 minutes it is ready to pass traffic (the former up to 7 minutes). I patched my cables over, cleared the ISP router ARP cache and immediately I was in business on the new hardware.
It was a great relief and always satisfying to get it right first time. After leaving 72hrs to ensure stability I'll arrange for the secure and responsible destruction of the existing hardware.
CND has many years of experience securing clients with firewall platforms and other components forming a robust security posture. If you need help replacing or upgrading EoL platforms please get in touch, we are always keen to help clients on such tasks.