CND News and Blog
Boston here we come! For those who've not yet had the opportunity to travel to a Splunk .conf event, it really is an event to behold. Big corporations with stock market listings are often necessarily conservative and perhaps, a bit dull. Splunk has none of that going on, if you're a cyber security professional this is a great annual occasion to rea...
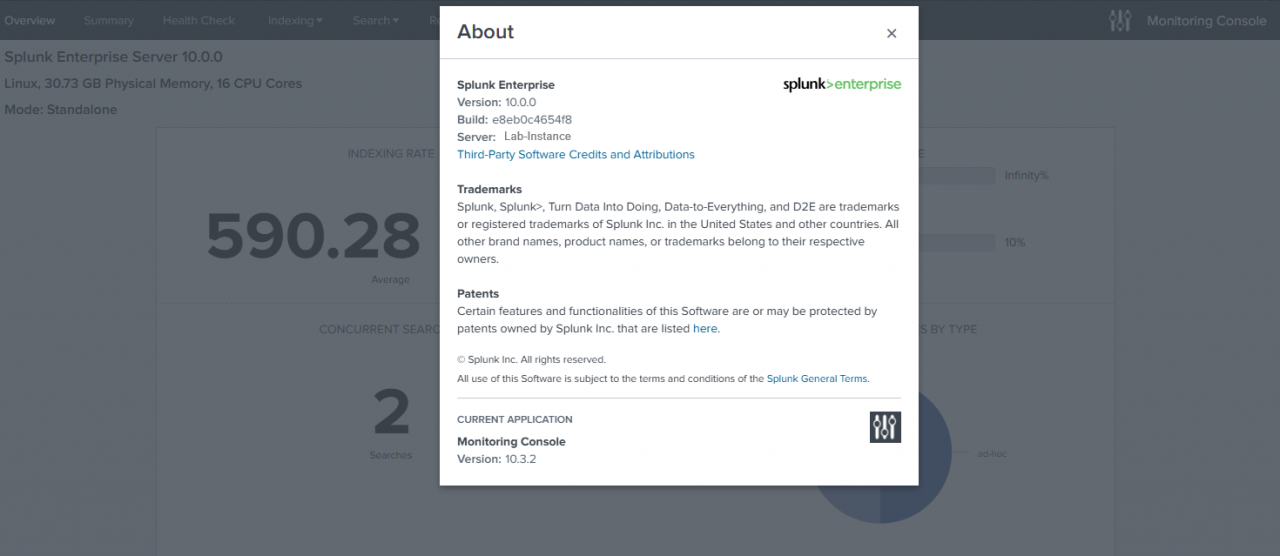
Splunk reaches double digit maturity! I was very surprised on Tuesday to receive a nudge from a fellow Splunk Professional Services (PS) consultant, saying that Splunk 10.0 had been released overnight with almost no fanfare or mention. Splunk first released their Data-to-Everything platform in 2004 and has been ingesting data logs as the leadi...
A couple of weeks ago a new version of Splunk was released: 9.2.2, this included various CVE resolutions (URL) and many of our clients have already rapidly responded and upgraded their version of Splunk. Upgrading is a quick and fairly low effort, low risk exercise so long as you haven't allowed tech-debt to creep into your infra. However once your...
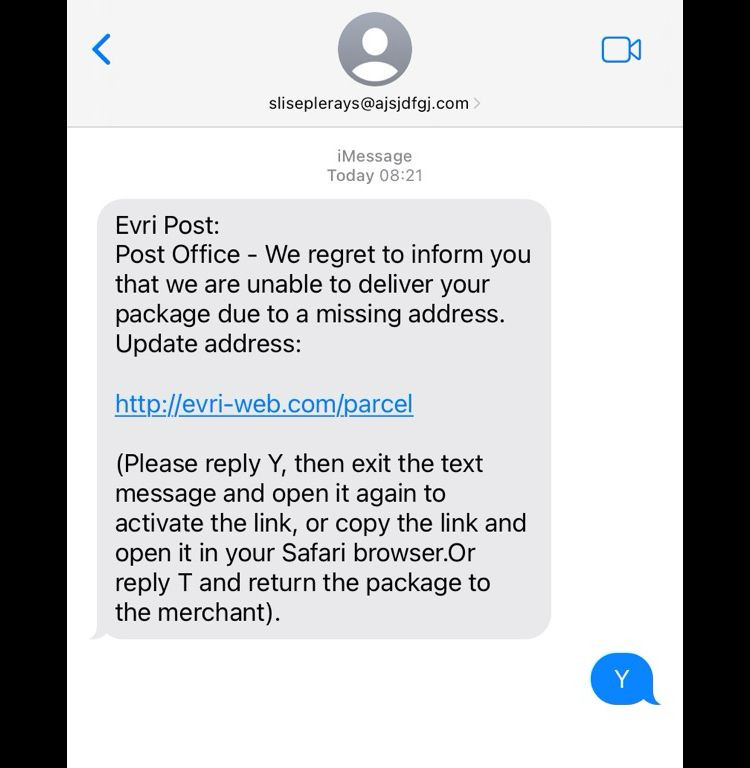
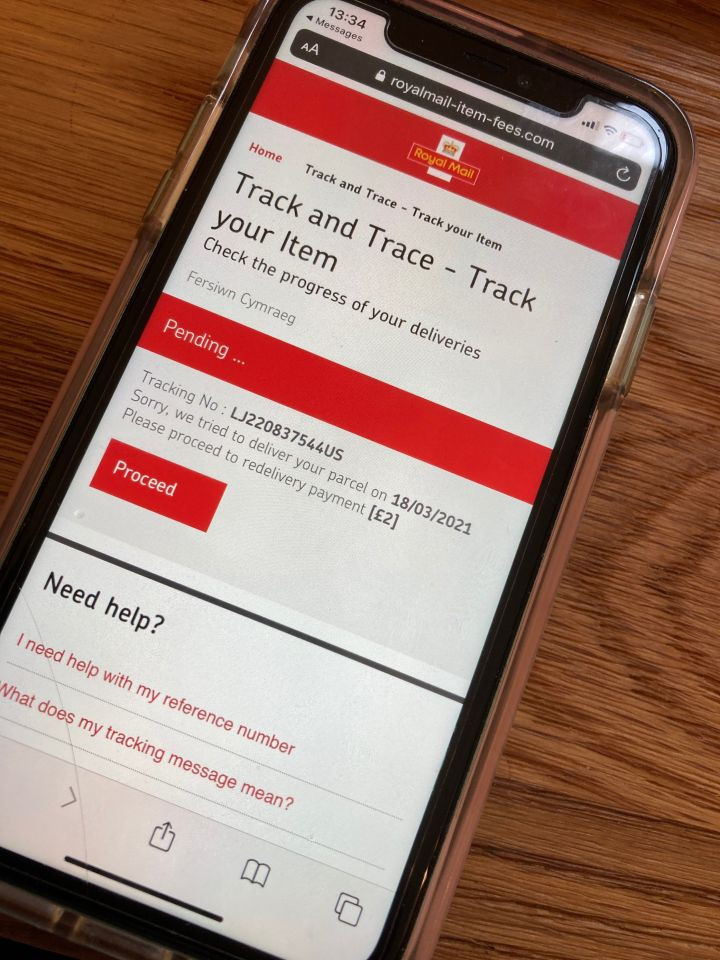
Scamming is sadly a daily risk whilst navigating cyberspace. I wrote almost exactly 3 years ago in different post about a similar postal scam, masquerading as the Post Office asking for a small missed delivery fee (URL). Well this week it happened again to a family member who started to fall for it, fortunately they stopped but ...
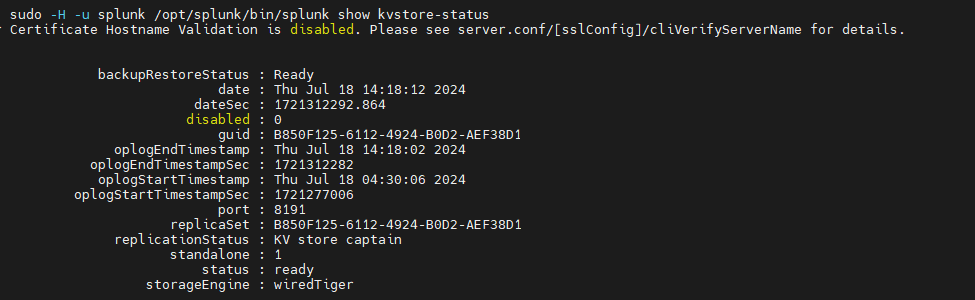
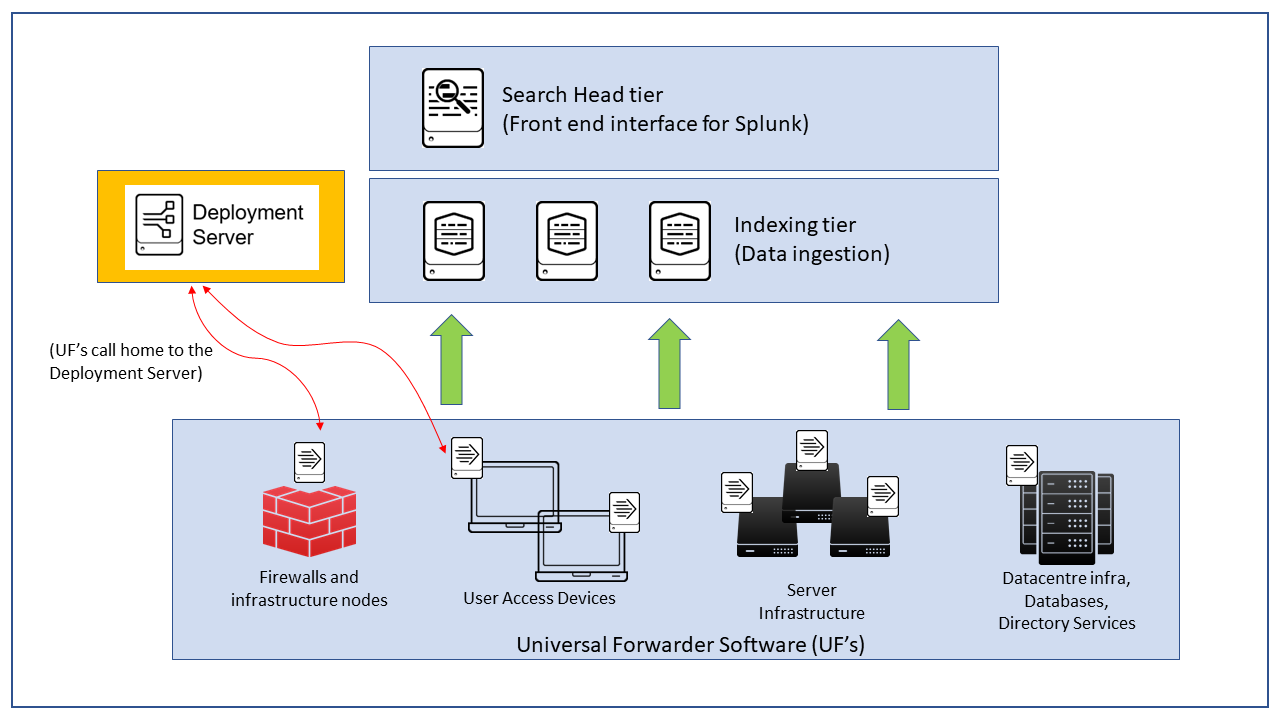
TLDR: Building a Splunk Test instance is really useful, helps protect against prod outages and very performant hardware is now available for a fraction of the price it used to be; if you're willing to deal with some tech challenges! Splunk Test instance Many of our clients rely on Splunk as their production SIEM tool to monitor, detect and respond ...
As my PA-220 firewall heads towards EoL I swapped it out for a PA-410 and OS 11.x I've worked professionally with firewall platforms for nearly 20 years, during that time I've configured Netscreen, Juniper, Palo Alto and Cisco to name a few of the dominant vendors. The most admin friendly and enjoyable platform to work with in m...
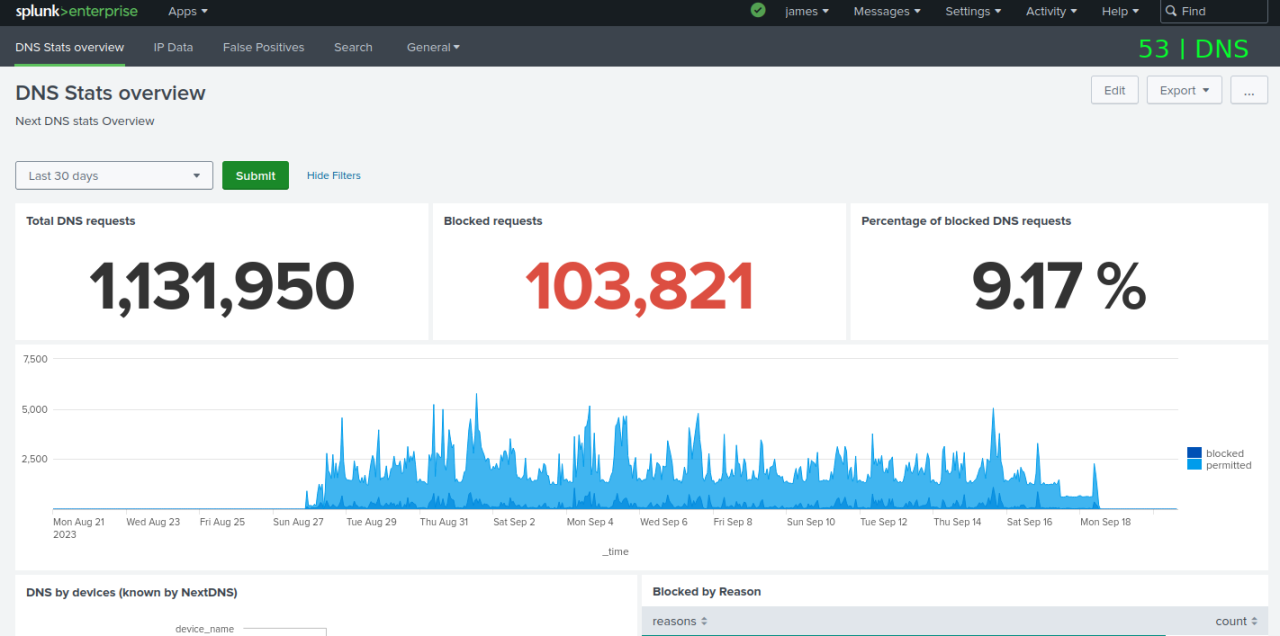
I was listening to an InfoSec podcast on the drive back from a client recently (Privacy, Security & OSINT Show) it's a really good listen and I really appreciate Michael Bazzells work. One of the items in the podcast was NextDNS, a product which I've not come across before. NextDNS operates by you registering an account for a very mod...
TLDR: Excellent technical conference with great opportunities for meeting other Splunkers, sound in-depth technical workshops with a good deal of content to follow up on and study. Splunk as a tech company manages an effortlessly relaxed corporate culture that is very enjoyable to be a part of. Intro: This was to be my first global scale tech confe...
My family and I moved home last week and everyone knows what a chaotic and stressful time this can be. There are in-fact quite a few cyber threat vectors when moving and during the move process my conveyancing solicitors e-mail server was targeted by a threat actor; the goal of this is to persuade would be buyers and sellers to ...
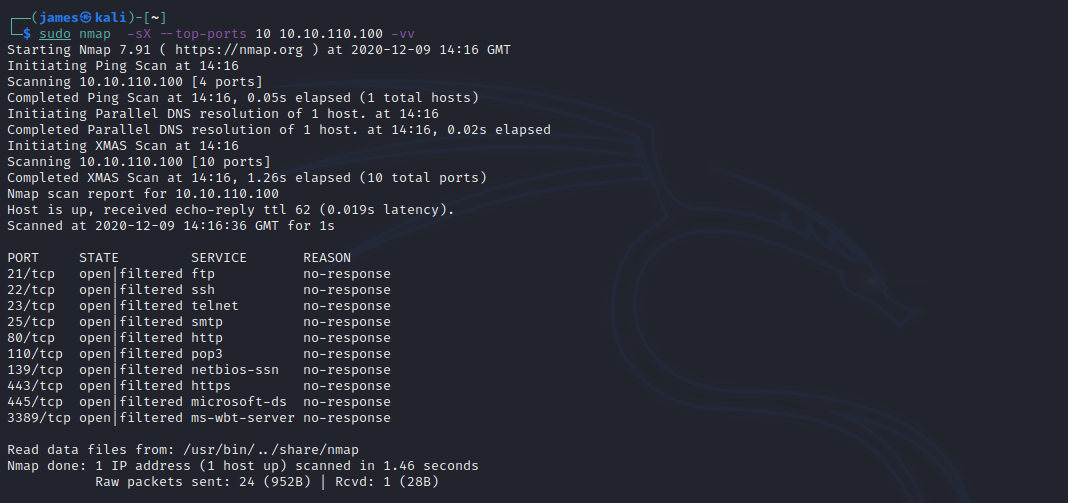
Brilliant it's nearly Christmas and I'm sure everyone is looking forward to a good break and sigh of relief over the Christmas break. However there is one festivity that takes place year round (no it isn't festivus for any Seinfeld fans out there), I'm of course talking about xmas tree scanning. This is a type of port scan whereby your threat ...
Last week saw Splunk .conf 2020 take place and instead of a Las Vegas venue it swapped to a virtual event, as with so much as an effect of Covid-19. This was my first Splunk .conf event and for the un-initiated there are a huge variety of talks, in all 230 this year and obviously the focus for myself and CND colleagues was on cyber security related...
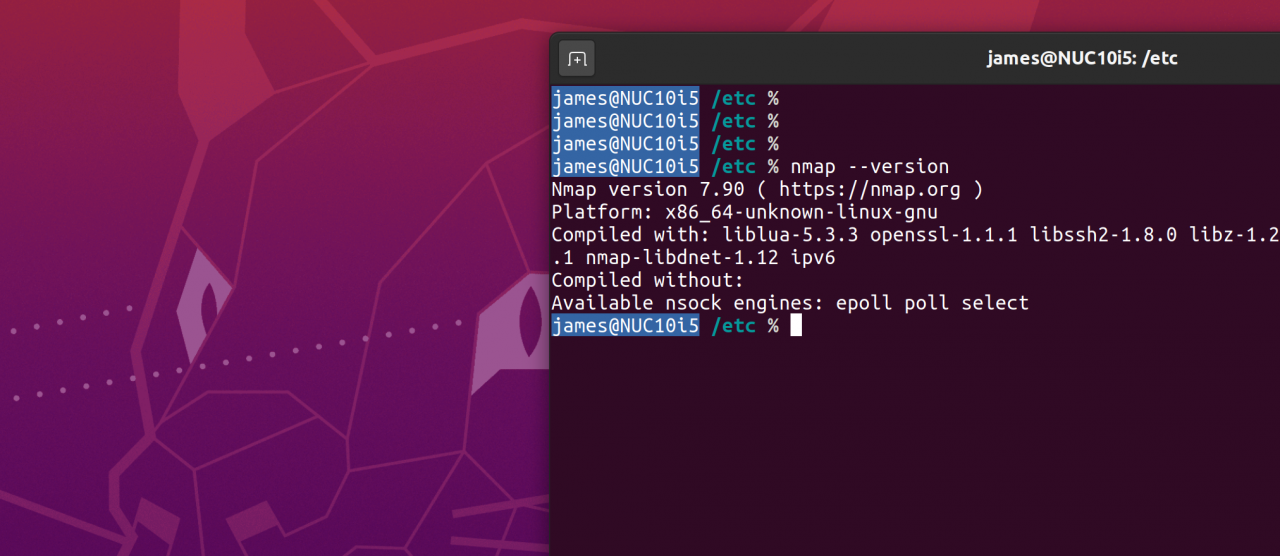
This week saw the release of Nmap 7.90 although as yet my particular Linux distro repository has yet to be updated (manual installation thus required). For security professionals it's worth reading the full release announcement here (URL), there are some significant changes and impressively the number of OS fingerprints is up to 5,678. If you've st...
By accepting you will be accessing a service provided by a third-party external to https://www.cndltd.com/