My family and I moved home last week and everyone knows what a chaotic and stressful time this can be. There are in-fact quite a few cyber threat vectors when moving and during the move process my conveyancing solicitors e-mail server was targeted by a threat actor; the goal of this is to persuade would be buyers and sellers to send their life savings to a new bank account with great urgency in order to complete their sale. Sadly some people fall foul of this each year and lose a very significant amount of their personal wealth (I commend my particular solicitor for their efforts to combat and inform their clients against such awful scams).
Being a cyber security professional I'm very careful and ensure I use best practices such as compartmentalised passwords, multi-factor authentication and a password manager. This coupled with physical countermeasures such as a decent level 4 shredder and careful data hygiene should keep one below the cyber parapet for the most part.
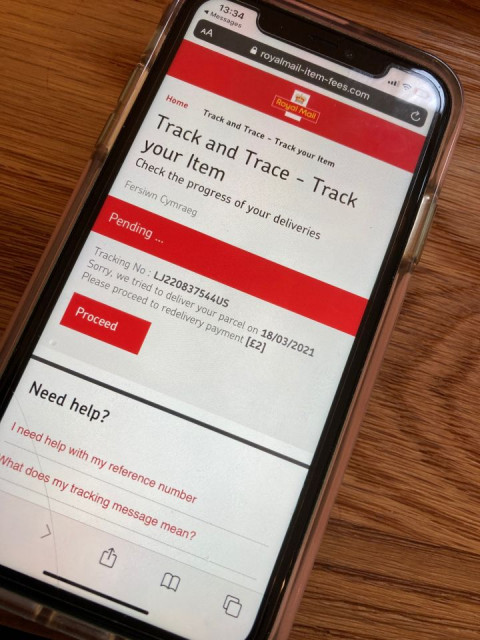
However even with all this care and attention it only takes one short lapse of attention to take a turn down a cyber dark alley. My wife mentioned to me at lunchtime in passing that she couldn't find her bag in between all the moving boxes and could she borrow my debit card to pay Royal Mail for a failed delivery, of course I replied and left her to carry on. After a few minutes she said that's a bit odd why do they need my bank details, sort code, account number and card details, we already have redirection? Immediately pausing she stopped and I quizzed her.
The notification was via an SMS message and the parcel doesn't exist, the whole thing was a well crafted website cloning scam trying to extract as much personal data as possible. Luckily she stopped very early on and there was no data sent. So far so good. I was immediately flustered though and realised that with our move my normal hardware firewall from a major vendor was not yet passing our Wi-Fi traffic as the AP is still in a cardboard box somewhere, but would it have helped?
How could I help as a cyber security professional?
My first check was to Cisco's Talos security site, I plugged in the URL at around 1330hrs and at that point it had no reputation and was a new URL. I reported the URL to trustedsource.org (McAfee) as well as Cisco and immediately sent it up to these two major providers to publish as a malicious URL. As of 2030hrs it now shows accordingly:
- Reputation Lookup || Cisco Talos Intelligence Group - Comprehensive Threat Intelligence
- Check Single URL (trustedsource.org)
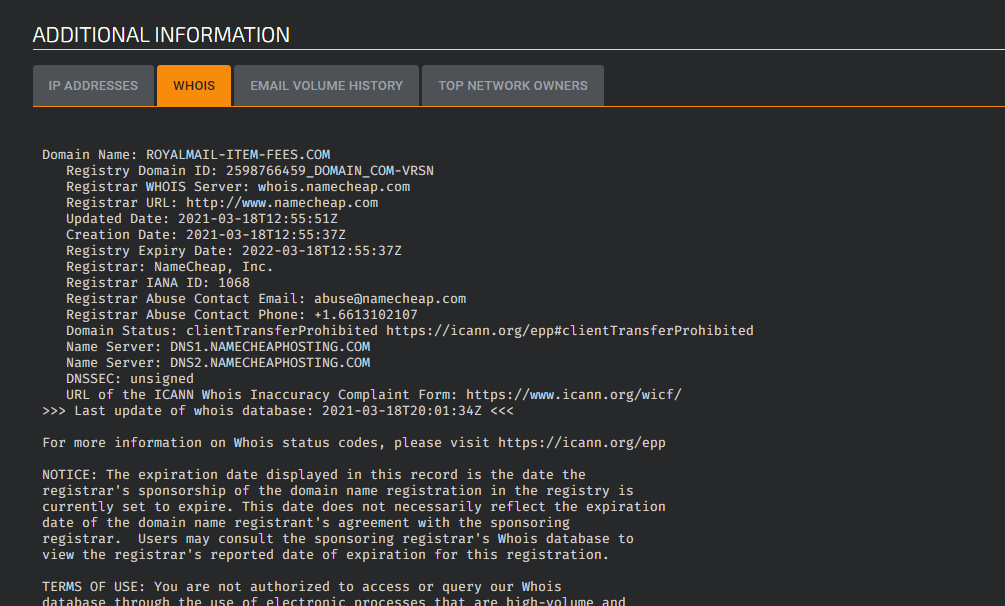
Looking at the WHOIS data the URL was registered at 1255hrs today (18th March 2021) and my Wife received the malicious SMS prompt at approximately 1325hrs, just 30 minutes later. This is clearly the work of an organised cybercrime gang. I also followed up with an e-mail to the registrar abuse contact and am currently awaiting a response.
But the answer is no, my major vendor firewall with live URL updates would not have protected our home personal devices during the short window during which it was unclassified (unless one takes the security over connectivity approach of blocking all domains without a reputation score; this may well be sensible for businesses).
Below is an excerpt of the WHOIS data:
This is sadly a game of 'whack-a-mole' and I suspect that the cyber criminals having invested in this particular URL for Royal Mail will simply register similarly legitimate sounding domains using the same content and different hosting providers, as the site becomes automatically associated as malicious and high risk.
In this instance it is targeting consumers and not businesses but what if it just shifted focus slightly in terms of audience and targeted employees of a commercial organisation for a different service. CND provides professional Phishing Assessments as a service and sadly the first internal assessment often has a worryingly high click-through rate. The key here is education and awareness training and not finger pointing 'bad employees', with development and education the level of effort a would be scammer would need to put in goes significantly up and it becomes that much harder to successfully attack.
If you're concerned by this or any other issues, please get in touch. We can help.
Update as of 23rd March
- Sadly the registrar responded relatively positively, but placed a significant burden on the reported before they were willing to engage. They did not remove the domain.
- I note that it also made the front page on the BBC today: Fresh warnings over Royal Mail parcel scam - BBC News