Brilliant it's nearly Christmas and I'm sure everyone is looking forward to a good break and sigh of relief over the Christmas break. However there is one festivity that takes place year round (no it isn't festivus for any Seinfeld fans out there), I'm of course talking about xmas tree scanning. This is a type of port scan whereby your threat actor or purple team cyber security professional sets up a scan against the target node with multiple flags set.
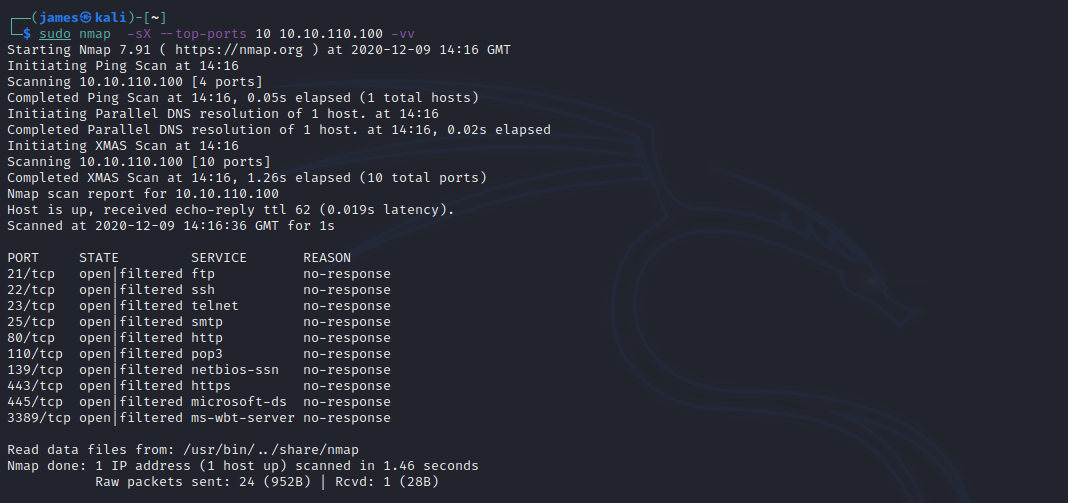
This is very straightforward to do and is well defined in nmap using the 'sX' flag (URL) and yes the X stands for xmas. This information gathering switch is all to do with how the original RFC (URL) was written in 1981. Below I have demonstrated an xmas tree scan in a pen testing lab environment (be sensible before you try this at home). This node is apparently a windows 2012 server but the key here is that each OS and build will react differently to this type of scan, and a threat actor may be able to glean useful data on their journey along the cyber kill chain using this and other enumerations. There is a good SANS white paper here (URL) on the cyber kill chain if this is a new term to you.
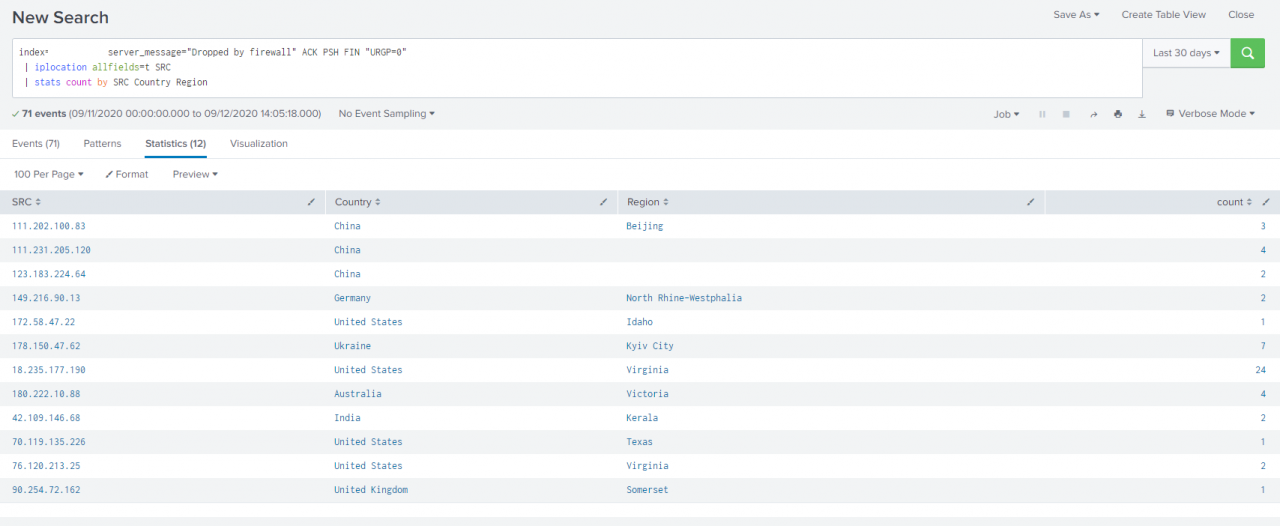
So having established what an xmas tree scan is and why it may be run, what does it look like from a Blue Team (URL) point of view? Well below is a stats table from one of our Splunk instances showing how to spot 'ACK PSH FIN URG' packet combinations. I've then simply used Splunk's 'iplocation' function and carried out an indicative location lookup based upon IP. We can see a large international dispersion of originating sources below over a 30 day period.
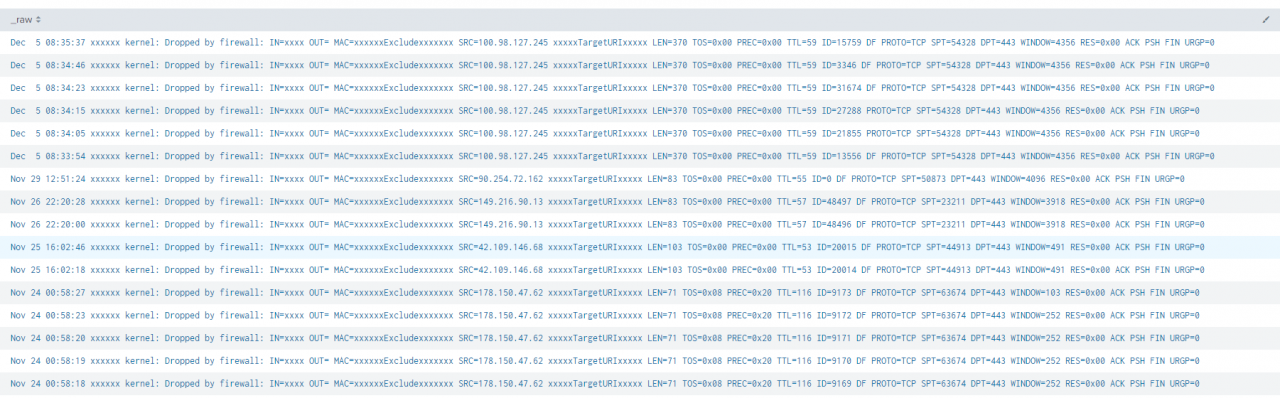
Looking at the raw syslog traffic which has been redacted for OPSEC purposes, we can see what this looks like to our servers firewall. Some of these include the addition of DF relating to fragmentation of the packet:
So wrapping up this exceptional year and on just another day in the 21st centuries cyber wild west, albeit a day which saw Fireeye's Red Team tools stolen by a nation state backed hacking crew (URL) spare a thought for your infrastructure this Christmas. It will no doubt be receiving -sX packets all year round and whether you're looking for them or not in your logging, it's still happening and in some cases your infra will send the gift of metadata back.
If you're concerned about the threats highlighted in this article get in touch, we can help.